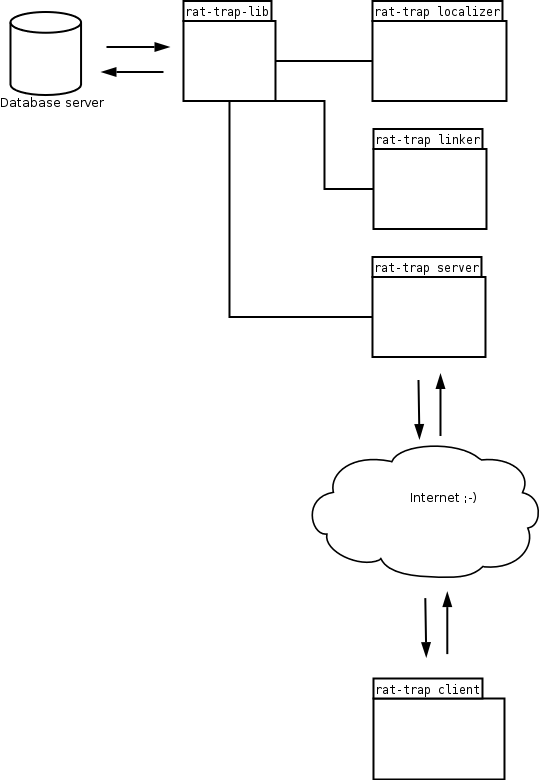
How does the rat-trap spam-tracking system work?
Before we start with the explanation of the interaction during the tracking-process we will describe of which components the system consists and what they do.
Lure-website
The first step of the spamtracking process is to offer email - addresses to potential email harvesters. a new email - address is generated for each access to the lure-website. This address is contains encoded information about the harvester's ip - address and the exact time of the access. All email - addresses will point to one (previously configured) email - server. You will need a catch-all capable account on that server to download all those messages with the rat-trap server.
The addresses are displayed in multiple ways of decoding (e.g. ASCII, hexadecimal, textual representation). Depending on which address - type the system will receive spam-emails it can determined how much intelligence the harvester invested in finding potentially hidden or encoded email-addresses.
All accesses of email-harvesters or human visitors will be transferred to the server via XML-RPC. The recorded access will be used by the linker - component.
Linker
Depending on the configuration of your crontab - entry the linker component will be executed in certain intervals. Each time it is called it will use the catch-all email-account to download all new spam-emails. Then the linker will extract the encoded ip-address and timestamp from the email-adress of each received email. If the linker finds a matching access for that ip-address and timestamp in the access-log of the lure-website it will create a linking - entry that represents the relationship between the spamm - sender and a email - address harvester.
Localizer
During the linking - process the hostnames of the harvester and the spam-sender will be stored in the database. Since the client shall show the location of spammers and harvesters on a worldmap some geographical location information is needed.
This information is retrieved by using the analysis of the data returned by the common traceroute command. If the traceroute returns insufficient data a simple ip to country conversion is used as a backup solution.
Server
The Server mainly contains of two servlets that implement an XML-RPC webservice. Those servlets are accessed by the lure-website and the visualization - client.
Client
Since the client uses the XML-RPC interface of the server its implementation is totally independent of the server. It simply fetches data from the server and displays it in a nice way. The client which is shipped with the rat-trap spamtracking system is based on Thinlet and needs a Java Runtime Environment. The documentation contains further information about the data - structure of the XML-RPC data that is provided by the rat-trap-server
UML - Diagram
One diagram might tell more than thousand words. :-) Study the following diagram to learn about the global relationships between the rat-trap components.